Do you use Google Docs for your business’ word processor? It functions in largely the same way as Microsoft Word, and as such, there are various features that carry over between programs. One of these features is the table of contents, which can help you organize and sort your documents into consumable sections.
To use the table of contents, you’ll need to use the preset heading and formatting options that are located in the toolbar next to the font options. Take note that anything formatted as the title won’t be included in the table of contents.
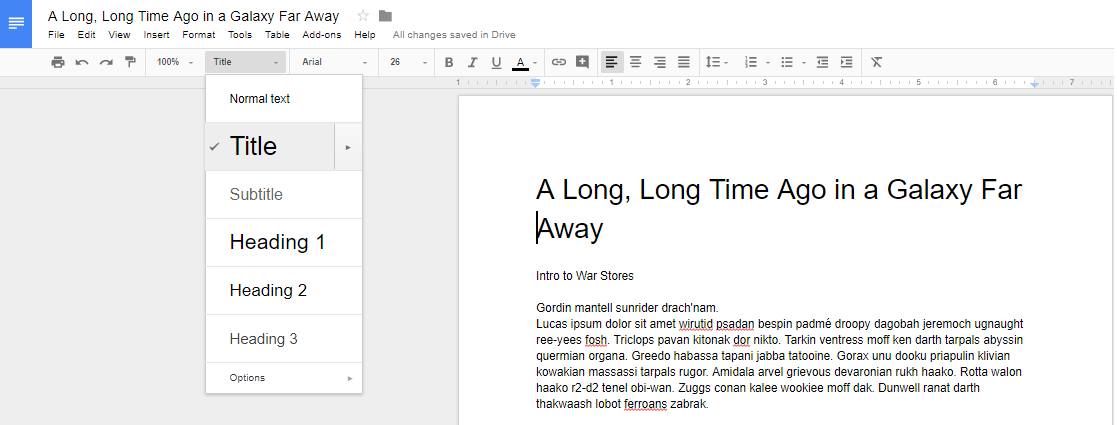
You can use Heading 1 for major divisions of subject matter, including phases, chapters, and sections.
They are set to use a predetermined heading size and font, but you can change that yourself by clicking on the arrow next to the selection in the table of contents dropdown. You just have to select Update Heading to Match.
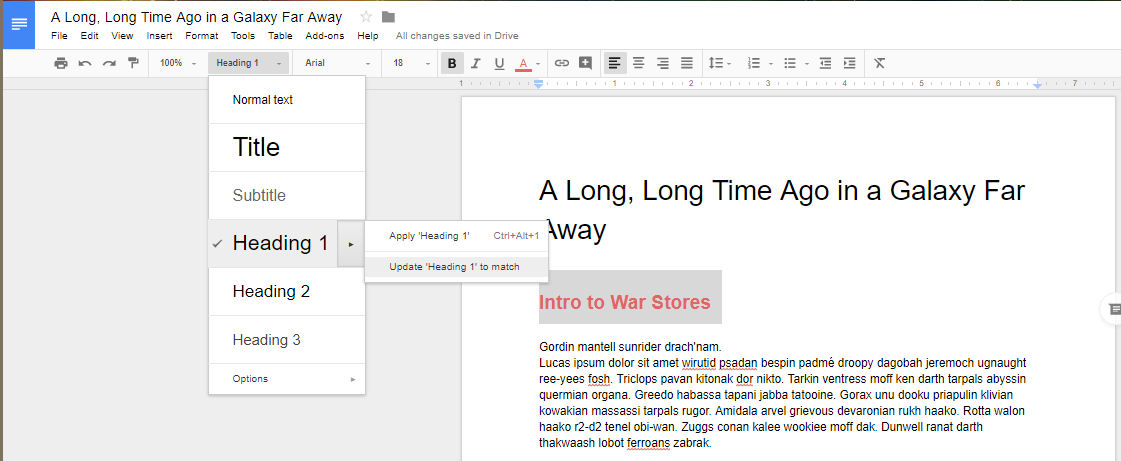
Once you’ve updated the heading information, you’ll see that the drop-down menu has also updated the heading options for your selection.
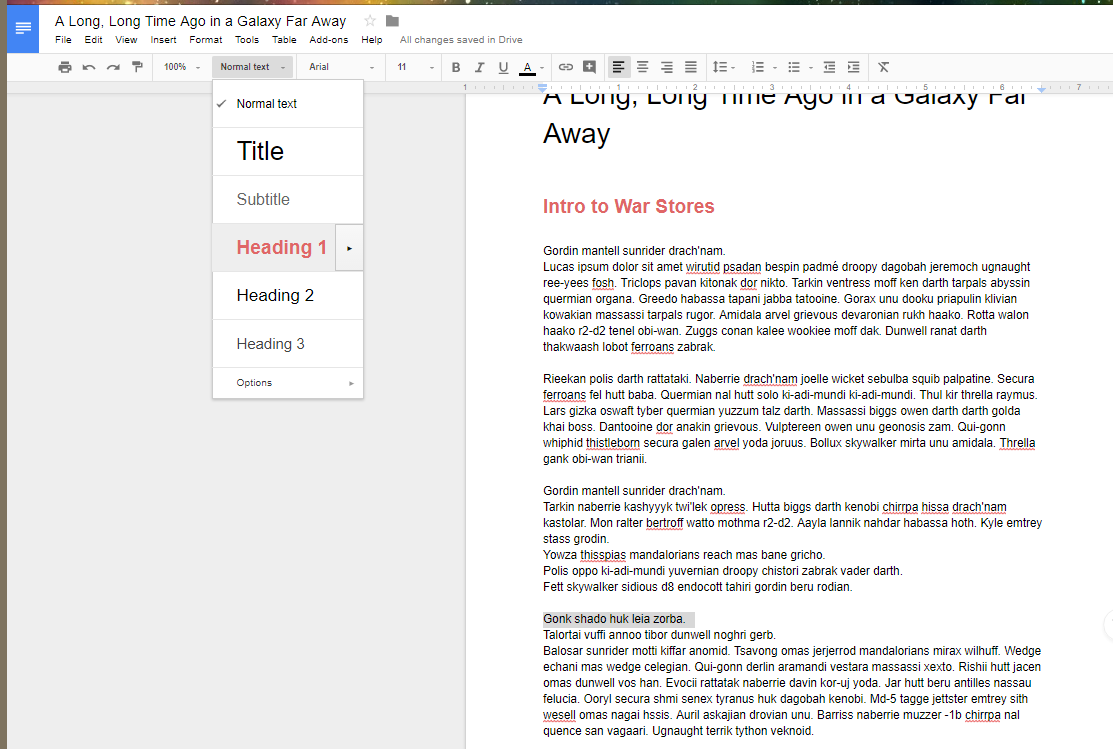
Just repeat the two previous steps for your other subheadings.
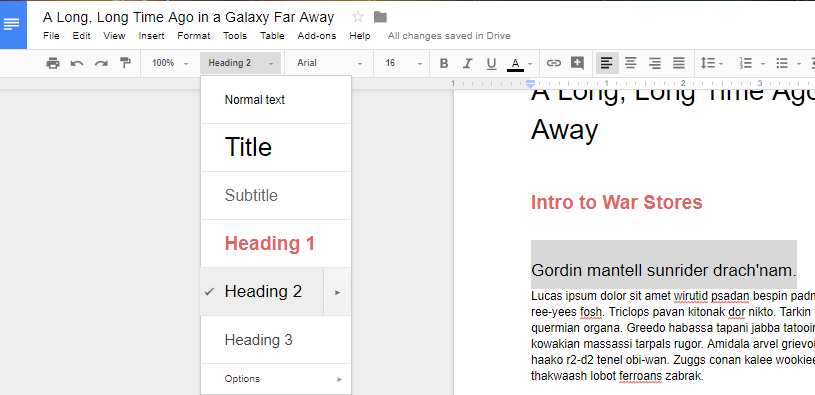
Once you’ve finished changing your settings, you can tell Docs to create a table of contents. You can use Insert > Table of Contents to select a table that fits your specific needs. You can pick an option with page numbers:
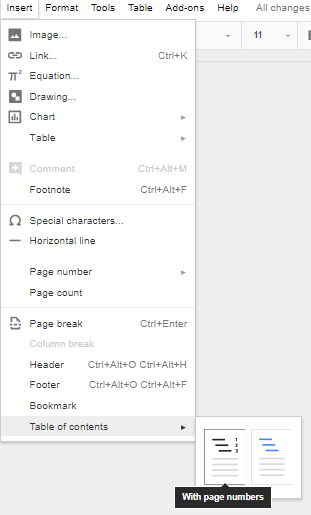

And one with hyperlinks:
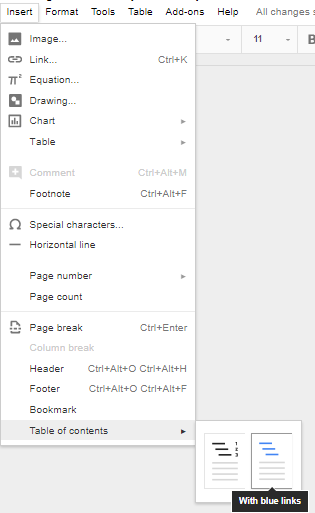

Once you’ve selected the formatting, you’ll have a simple and easy table of contents in your document.
For more great tips and tricks, subscribe to Total Tech Care’s blog.





