 If you own an Android device, you’re no-doubt aware that Google issued an upgrade to Android’s OS not too long ago. This update, dubbed Android 5.0 Lollipop, presents several aesthetic upgrades to devices which were running a previous Android OS. However, there were also some functionality changes, a few of which were less than desired; like the unexpected changes to Android’s alarm clock.
If you own an Android device, you’re no-doubt aware that Google issued an upgrade to Android’s OS not too long ago. This update, dubbed Android 5.0 Lollipop, presents several aesthetic upgrades to devices which were running a previous Android OS. However, there were also some functionality changes, a few of which were less than desired; like the unexpected changes to Android’s alarm clock.
Don’t Put This Tip “On Snooze”
Before the Lollipop upgrade, Android’s alarm clock application worked in silent mode. This was exceptionally useful, especially if you wanted to turn your phone’s sound off overnight to get a good night’s rest. However, in Lollipop, Silent mode is called Mute mode, where all sounds from calls, texts, and other notifications are silenced… including alarms.
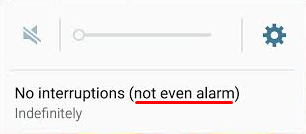
You don’t need us to tell you that this new functionality change can affect your ability to get to work on time in the morning. Thankfully, there’s a pretty simple fix to this problem, even if it’s not the most obvious solution.
Since Lollipop doesn’t allow alarms to go off in Mute mode, there’s an extra hoop you have to jump through in order to get them to work properly. You can set your phone to only go off for what are called Priority Interruptions. Because alarms are always considered priority interruptions, you shouldn’t have to worry about the alarm being silenced.
To activate Priority Interruptions, turn up your volume to Sound or Vibrate. Next, select Only allow priority interruptions.
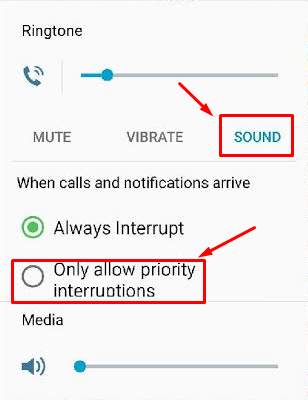
Doing this opens a menu beneath your selection. Then, click Settings.
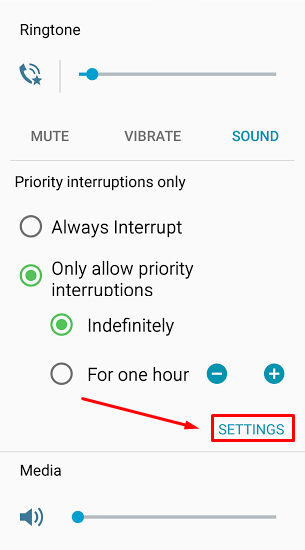
This lets you view the Priority Interruptions settings. Don’t be fooled by the Silent choice here; Priority Interruptions only work in Sound or Vibrate mode. If you really want a Silent mode similar to the previous version of Android, you can uncheck messages, phone calls, and reminders in Sound mode. This lets it basically act the same as it used to, more or less.
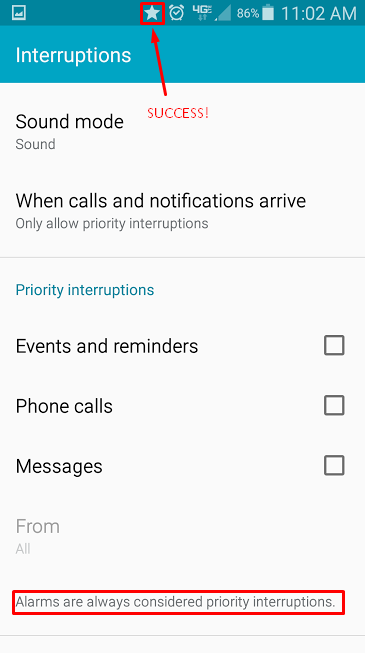
If you’re successful in setting your Priority Interruptions, a star will appear next to your alarm clock symbol at the top of your screen. Afterwards, it’s best to make a test alarm to make sure that it goes off as planned. It’d be a shame to go through all of this trouble just to miss your alarm. Of course, if all else fails, you could always get a dedicated alarm clock from your local department store; or, get a pet. Whichever works for you.
Be sure to subscribe to Total Tech Care’s tech blog for great tips every week.




