The popularity of Microsoft Word is undeniable, in part because it features preconfigured settings to make it easier for its users. While these settings are useful for most of these users, they might not reflect your business’ use of Word. Fortunately, you can make adjustments to these settings to increase the value that Word can offer your business. Here, we’ve put together some tips to help you make these changes, if you so choose.
Before we get started, we want to make sure that you know to consult with your IT department or provider before you go to make any of these changes. That way, they will be able to undo any mistakes you or your employees might make during the following processes.
Customizing Word’s Rules to Meet Your Preferences
It’s likely that there are some things that you regularly type into Microsoft Word that it may not agree with. Your company’s name might not exactly jive with the grammatical rules that the rest of the language should subscribe to, for instance, or you may prefer to stylize certain terms or phrases differently. Word isn’t going to like this, and is going to try to let you know that a mistake has been made. Of course, it might also just change the word you typed to what it is “supposed” to be.
These corrections can be a pain to repeatedly make, and there’s always the chance that one will be missed. Fortunately, Word offers you the opportunity to “teach” it new rules via a fairly simple process.
To access these rules, select File, and from there, Options. A new window should pop up with a Proofing option in the list. That page looks like this:

Adjusting AutoCorrect
Here, you can alter a variety of proofing options, including your AutoCorrect Options. Clicking that button will present you with another window.
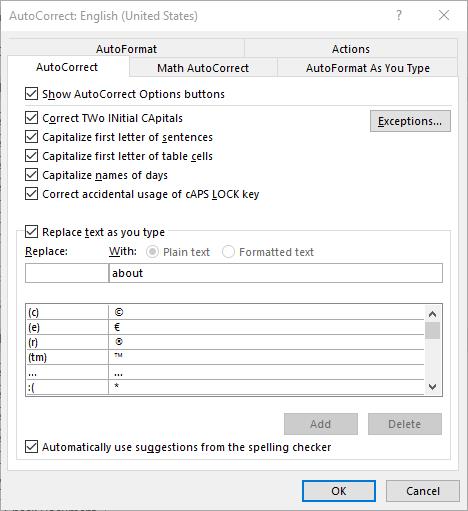
This window allows you to set your AutoCorrect rules, identify any exceptions you might want to make, and review how misspelled text can be automatically revised.
Establishing Grammar Rules
Returning to the Proofing List window, you also have other options that allow you to adjust Word’s corrections. For instance, clicking the Settings... button under When correcting spelling and grammar in Word provides another window. From here, you can control which grammar rules Word will flag or ignore in your copy.
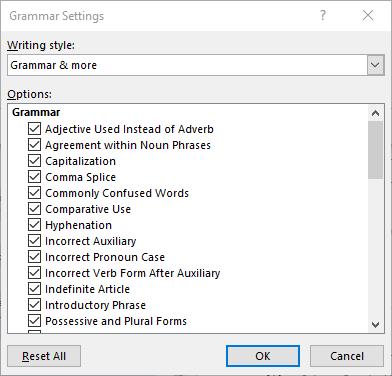
Stop Worrying About Word Changing What You Write
By implementing these changes, you can prevent small annoyances from interrupting you as you work with Microsoft Word. This way, you can accomplish more without having to worry about dealing with automatic corrections again.
For more tips on how to best leverage your solutions to save you valuable time and money, subscribe to our blog!





