 For those of you who don’t yet have Windows 10, don’t panic. It’s not going anywhere, and you’ll get it soon enough. In the meantime, it’s important that you don’t get impatient and hastily open suspicious emails containing what appears to be a launcher for your Windows 10 download. Hackers are using ransomware to extort money from unsuspecting users who just want their new operating system already.
For those of you who don’t yet have Windows 10, don’t panic. It’s not going anywhere, and you’ll get it soon enough. In the meantime, it’s important that you don’t get impatient and hastily open suspicious emails containing what appears to be a launcher for your Windows 10 download. Hackers are using ransomware to extort money from unsuspecting users who just want their new operating system already.
For some, the fault might lie with Microsoft because of the way they’ve decided to deploy Windows 10. Making people wait even more for a product that already exists is somewhat maddening, and hackers are taking advantage of this impatience to strike. CTB-Locker is a ransomware similar to Cryptolocker, in which it encrypts information locally on your PC, and offers a decryption key in exchange for a hefty price.
This ransomware spreads via email. Victims will receive a message in their inbox which appears to be from Microsoft detailing how they can bypass the wait for Windows 10, and prompts them to download what appears to be a launcher for the new operating system. Once the user downloads the executable file, the malware starts encrypting data on the PC. The user is locked out of their PC until they pay the ransom.
Furthermore, if the user wants to regain access to their files, the ransom must be paid in Bitcoin, a cryptocurrency which is known for its anonymity and difficulty to trace. Adding to the difficulty is that the hackers are using the Tor anonymity network to communicate, which makes catching the clowns behind this act difficult at best. Ransomware is an increasingly popular problem, and according to ZDNet, it can cost users anywhere from $200 to $10,000 for each occurrence, leading to ultimate costs of up to $18 million. That’s a lot of cash that’s been extorted from some 1,000 users in 2015 alone.
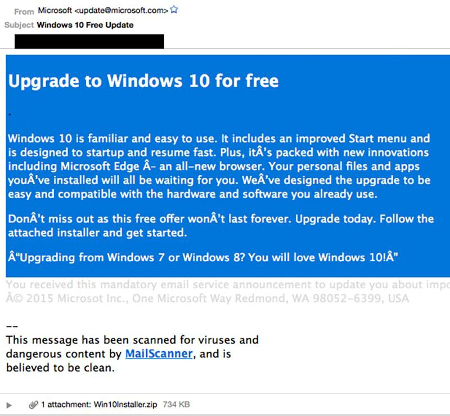
Of course, with a good email solution you won’t be receiving this message. A powerful spam blocking solution is capable of keeping spam messages out of your inbox almost indefinitely, meaning that you have little to worry about from the average phishing attack. Still, if a hacker wants to scam you bad enough, they’ll find a way to get through your security measures and attack you directly, in the form of a targeted spear phishing attack.
Therefore, the best way you can protect yourself from threats like CTB-Locker is to keep an eye on your inbox for any suspicious messages, and to never, ever, download attachments from unknown senders. Augment caution with a powerful spam filter and you’ll have all you need to keep phishing attacks at bay. Give Total Tech Care a call at 866-348-2602 to learn more.




