 The release of Windows 10 is fast approaching, and it’s suspected that it will arrive sometime this summer. However, Microsoft’s latest OS release, Windows 8.1, is still being left in the dust by Windows 7 in terms of sheer popularity and usage. What’s the current state of Microsoft’s Windows OS economy?
The release of Windows 10 is fast approaching, and it’s suspected that it will arrive sometime this summer. However, Microsoft’s latest OS release, Windows 8.1, is still being left in the dust by Windows 7 in terms of sheer popularity and usage. What’s the current state of Microsoft’s Windows OS economy?
ComputerWorld reports that two-thirds of all PC users are currently running Windows 7, as of last month. Based off of Net Applications’ monthly user share tracking, these are the statistics taken for the month of March 2015 concerning the different operating systems in Microsoft’s repertoire.
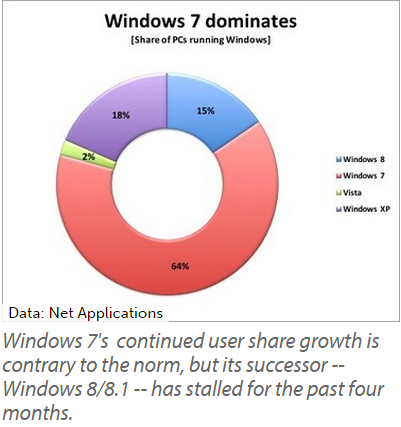
- 64 percent of users use Windows 7.
- 2 percent of users use Windows Vista.
- 18 percent of users are still clinging to Windows XP.
- 15 percent of users are using Windows 8 or 8.1.
Windows 7 is certainly a great operating system that has stood the test of time. Ever since it was released in 2009, it’s been a very popular choice amongst both consumers and business professionals. It was so well-received that it pulled support away from the overwhelmingly popular Windows XP, which lost patch and update support last spring.

However, Windows 8 and 8.1, the most recent of the Windows operating systems to be released, have failed to entice the end user into upgrading from Windows 7. If anything, Windows 7 is still growing more popular. As of this past February, 7 has seen a 2.6 percent increase, while Windows 8 and 8.1 have just about reached their limit over the past four months.
Even though Windows 7 still has a few good years left before its end-of-support date in 2020, all good things must come to an end sooner or later. Will Windows 7 follow in the footsteps of its predecessor, Windows XP, and have countless end users forsake upgrading for an unsupported system? If Windows 10 fails to take off, this might happen, leaving many users running without vital support patches and updates. This is why using a supported operating system is so important.
The next OS to hit Microsoft’s chopping block is the server OS, Windows Server 2003. However, the main cause for concern isn’t necessarily over security, but the complications of legacy hardware and software capability with new, modern machines and applications. It’s not always easy to predict what happens to your IT infrastructure when upgrading to a brand new server.
If your office is one of those that haven’t yet made plans to move away from Windows Server 2003, or if you’re running outdated operating systems on your business’s workstations, you should make arrangements immediately to start moving toward a more modern office. You can’t afford to fall behind, and Total Tech Care understands this. If you’re having a difficult time juggling your responsibilities as a business owner with incorporating imperative upgrades, we can help you manage and maintain your IT infrastructure. Just give us a call at 866-348-2602 to learn more.




