 If your organization hasn’t considered the cloud as a viable business solution, stop what you’re doing and check some recent statistics. You might be surprised to learn that cloud spending is the third-biggest IT expenditure. Such popularity shows that businesses are finding the benefits that the cloud has to offer to be substantial, and you too can take advantage of the cloud to more effectively leverage today’s technology.
If your organization hasn’t considered the cloud as a viable business solution, stop what you’re doing and check some recent statistics. You might be surprised to learn that cloud spending is the third-biggest IT expenditure. Such popularity shows that businesses are finding the benefits that the cloud has to offer to be substantial, and you too can take advantage of the cloud to more effectively leverage today’s technology.
According to the Worldwide Cloud IT Infrastructure tracker for the first quarter of 2015, cloud IT will soon surpass even traditional IT models sometime in the next ten years.
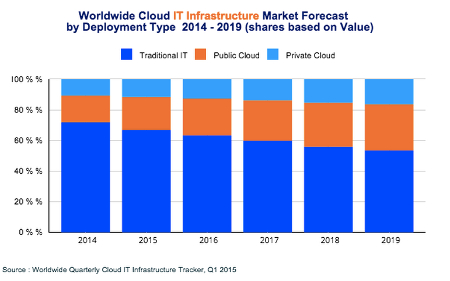
There are several noteworthy observations to make concerning this image:
- Traditional IT is still the main player for 2015, rolling in at just over 65 percent of all deployments.
- Public cloud IT accounts for around 20 percent of all deployments.
- Private cloud IT makes up over 10 percent of all deployments.
- Over the next five years, traditional IT will continue to decrease in usage, while the public cloud will make a significant jump in use. Private clouds will continue to grow, but not as quick of a rate as the public cloud.
On the financial scale, here are some statistics:
- Spending on cloud IT infrastructures will reach $33.4 billion in 2015 alone.
- Spending on private cloud infrastructures will grow to $11.7 billion.
- Public cloud shows projected expenditures and growth of up to $21.7 billion.
As these numbers show, the cloud isn’t something that successful businesses should ignore. It’s not a gimmick or a fad. It’s a legitimate IT infrastructure solution that vastly improves operations and procedures. If you want to take advantage of the future of computing, cloud IT should be a top priority. The benefits greatly outweigh the cost in the long run, and there are a plethora of options to choose from; be it private cloud, public cloud, or even a mix of the two in a hybrid cloud solution.
The cloud has the ability to provide maximum mobility for your business, effectively allowing your employees to access critical systems that they might otherwise only be able to access in-house. This provides more opportunities for productivity, especially while on the road for a business trip or conference. Your team can choose how they want to work, and when, so long as the devices can access the Internet and are approved beforehand.
With the cloud dramatically changing the way we view the deployment of information and applications, we want to hear your thoughts about this revolutionary technology. Contact Total Tech Care at 866-348-2602 for more information about how cloud computing can change the way your company works with technology.




