Google search is synonymous with searching the internet, but that hasn’t stopped them from constantly innovating the service. One of the most recent updates is to give users more context for the content that returns on search results. This works to protect users from potentially clicking on websites that could contain threats. Today, we discuss this innovation and how it will look to the end-user.
Google’s Page Widget
Google rolled out this feature on February 2nd, 2021. They now offer a widget that provides a look at a website before you click on it. You will begin to see three-dot menus appearing next to your search results. When accessed, it will give you the information that clicking on the link will take users to.
The information includes a blurb about what the website links to, including Wikipedia information, but if that isn’t available it provides Google’s own analysis as the site was last indexed. It also provides information about the website’s security.
This is what appears when you check the link for Facebook:
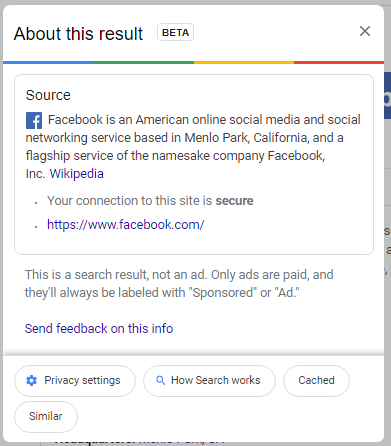
In this information, users can see that Google confirms that the website is secured, helps to protect data, and that the link was the result of the user’s search, and not an advertisement.
As things progress, this utility should be able to help users do a better job of choosing websites that don’t put their data, or your organization’s data, at risk. For more great security information and best practices check back to our blog weekly.





